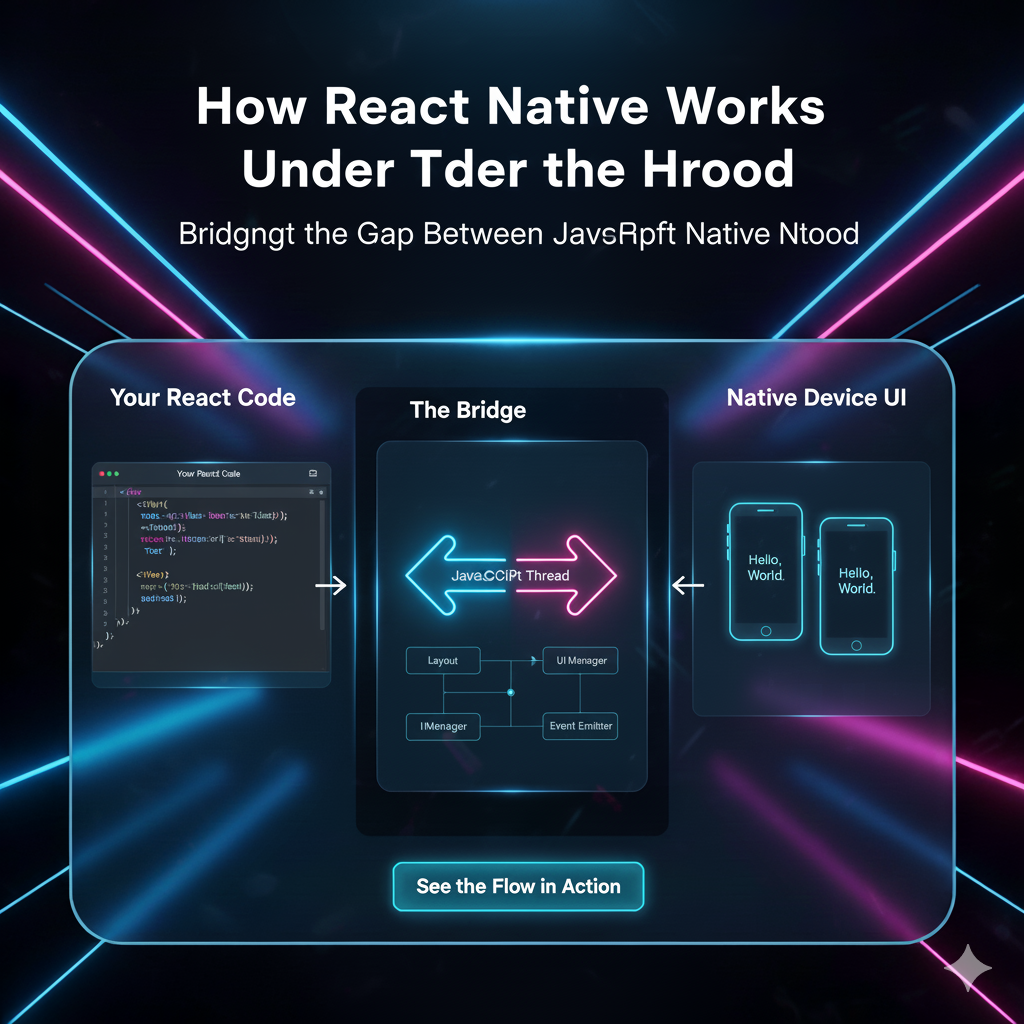
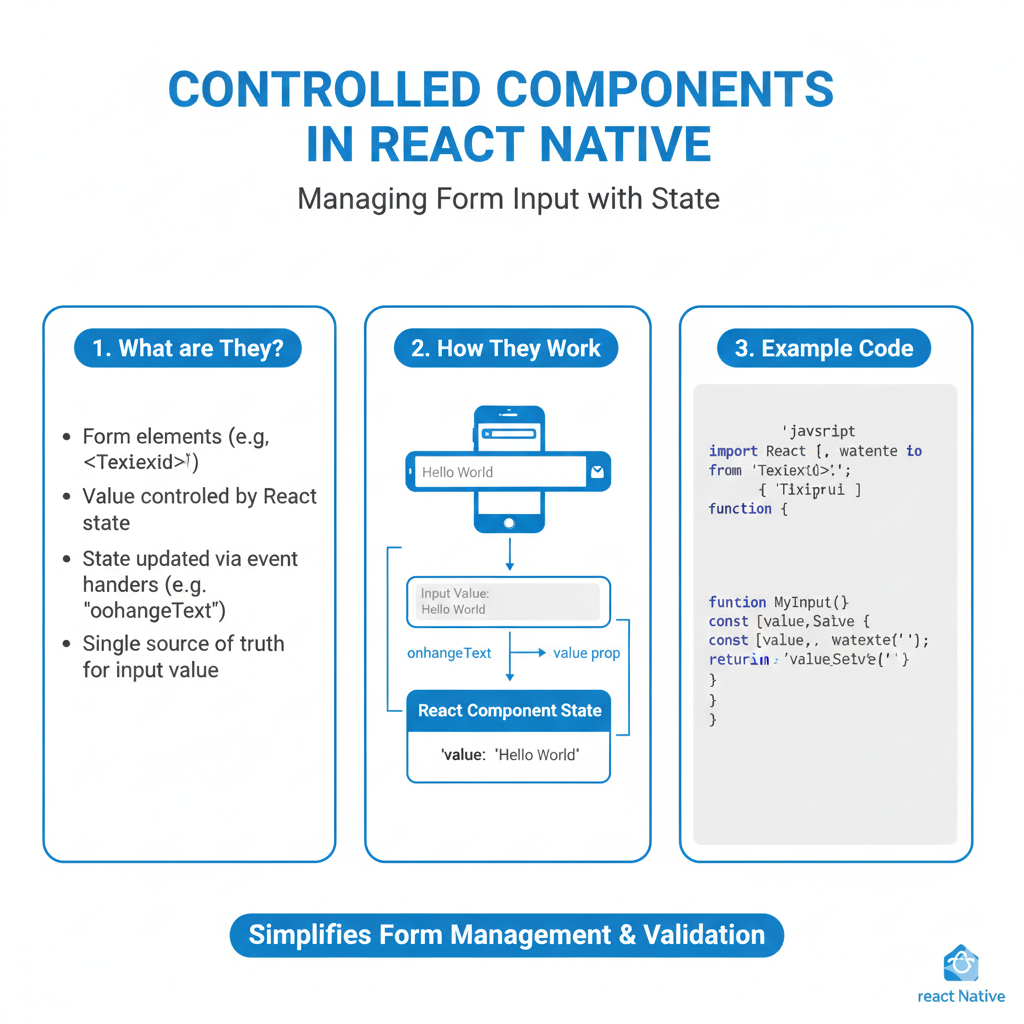
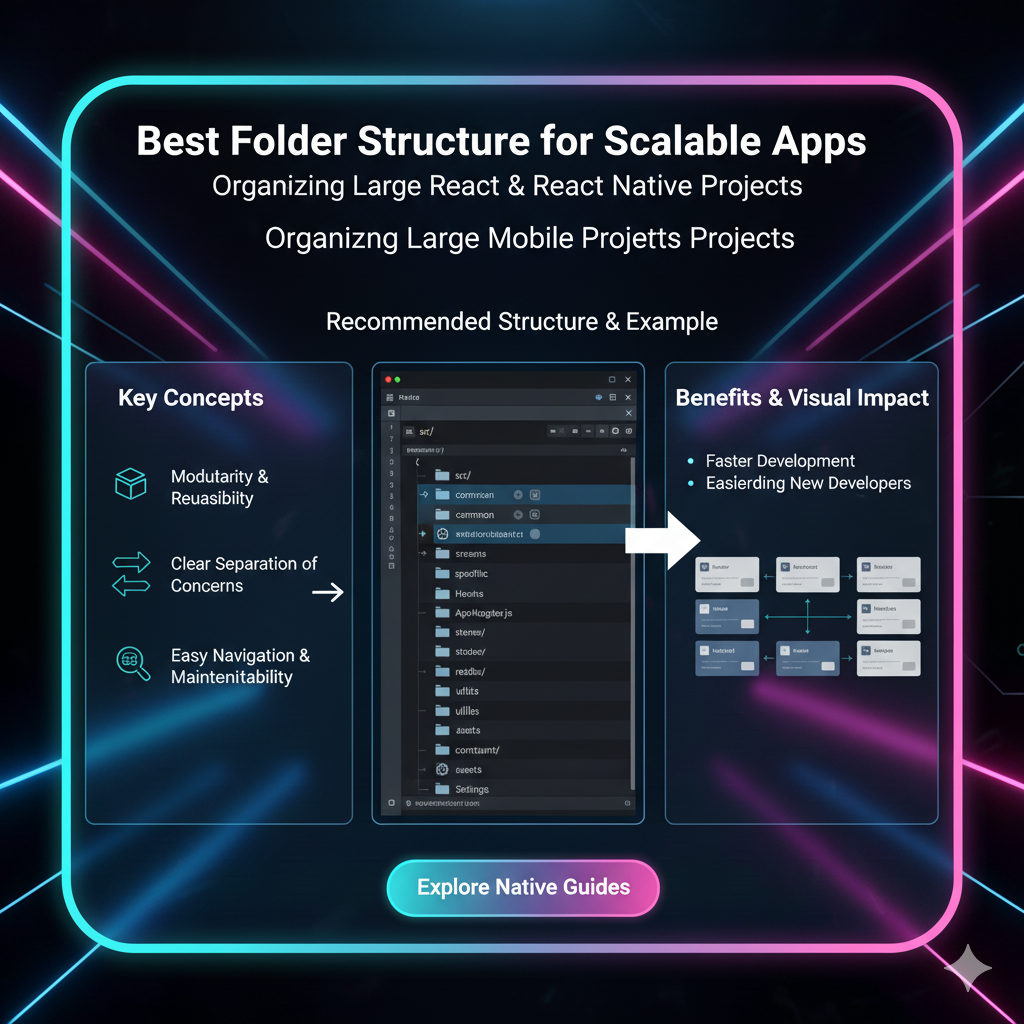
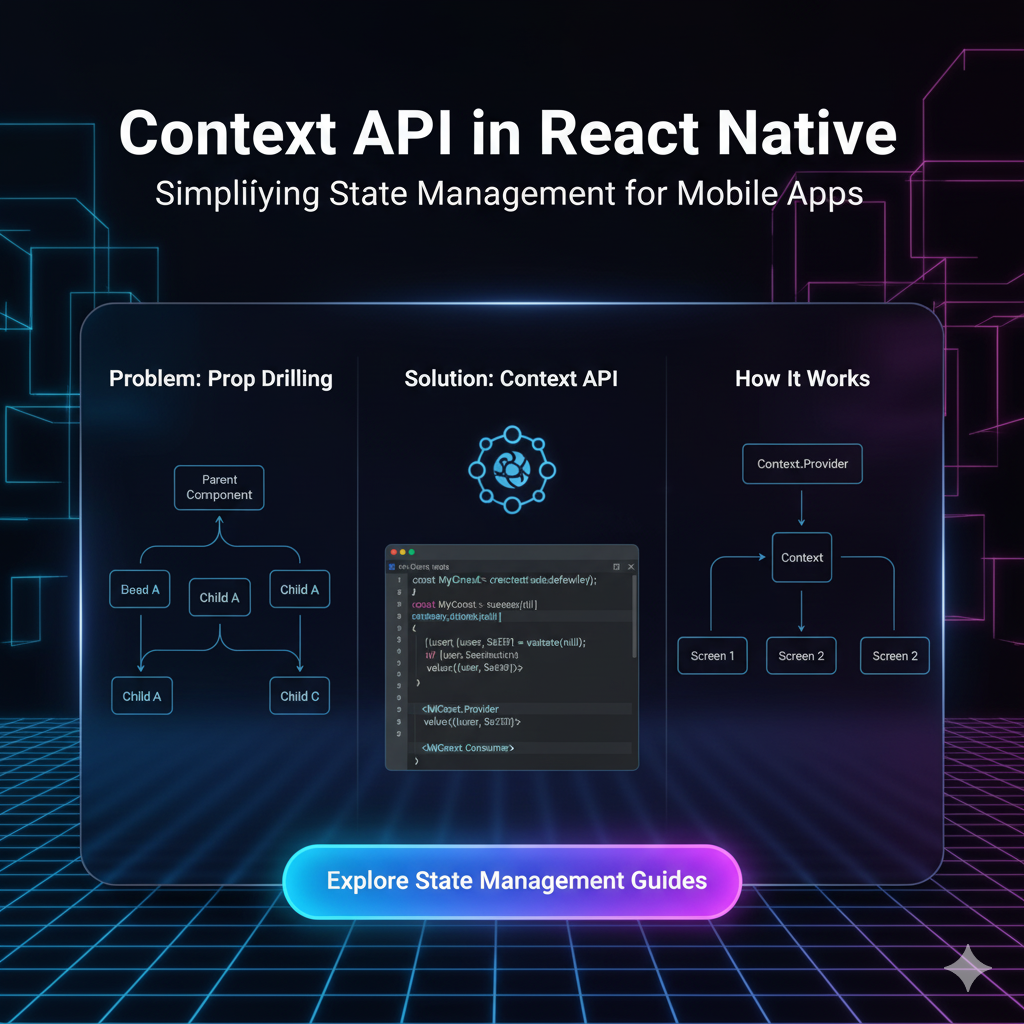
Secure Storage & Keychain 101: Why Your App Should Stop Storing Secrets in Plain Text
Tired of insecure app storage? Learn everything about Secure Storage & Keychain integration for iOS & Android. Protect user data with industry best practices. Enroll in CoderCrafter's dev courses today!
Lock It Down: A No-BS Guide to Secure Storage & Keychain Integration
Let's be real for a second. How many times have you quickly hardcoded an API key or saved a user's password in SharedPreferences or UserDefaults just to get a feature working? We've all been there.
But here's the cold, hard truth: in today's digital world, that's like writing your bank PIN on a sticky note and slapping it on your front door. Not cool, right? As developers, we have a responsibility to protect our users' data. A single security slip-up can destroy trust, wreck your app's reputation, and lead to some seriously bad press.
So, let's level up. This post is your ultimate, no-fluff guide to Secure Storage and Keychain Integration—the right way to handle secrets on mobile devices. We're breaking down the tech, the code, and the mindset you need to build apps that are actually secure.
What Exactly Are We Trying to Protect?
Before we dive into the "how," let's clarify the "what." Secure storage isn't for your cat pictures or generic app settings. It's for the super-sensitive stuff that, if leaked, would be a catastrophe.
Authentication Tokens: Those JWTs or session tokens that keep users logged in.
Passwords: Even though we shouldn't be storing raw passwords (use hashing!), sometimes we need to for biometric auth or similar flows.
API Keys & Secrets: Keys that give your app access to third-party services like Firebase, Stripe, or AWS.
Encryption Keys: The master keys you use to encrypt other data within your app.
Credit Card Information: (Handled with extreme care and PCI-DSS compliance, often using specialized services).
Storing these in plain text in a local database or a simple preferences file is a big no-no. It's the low-hanging fruit that hackers and malicious apps will target first.
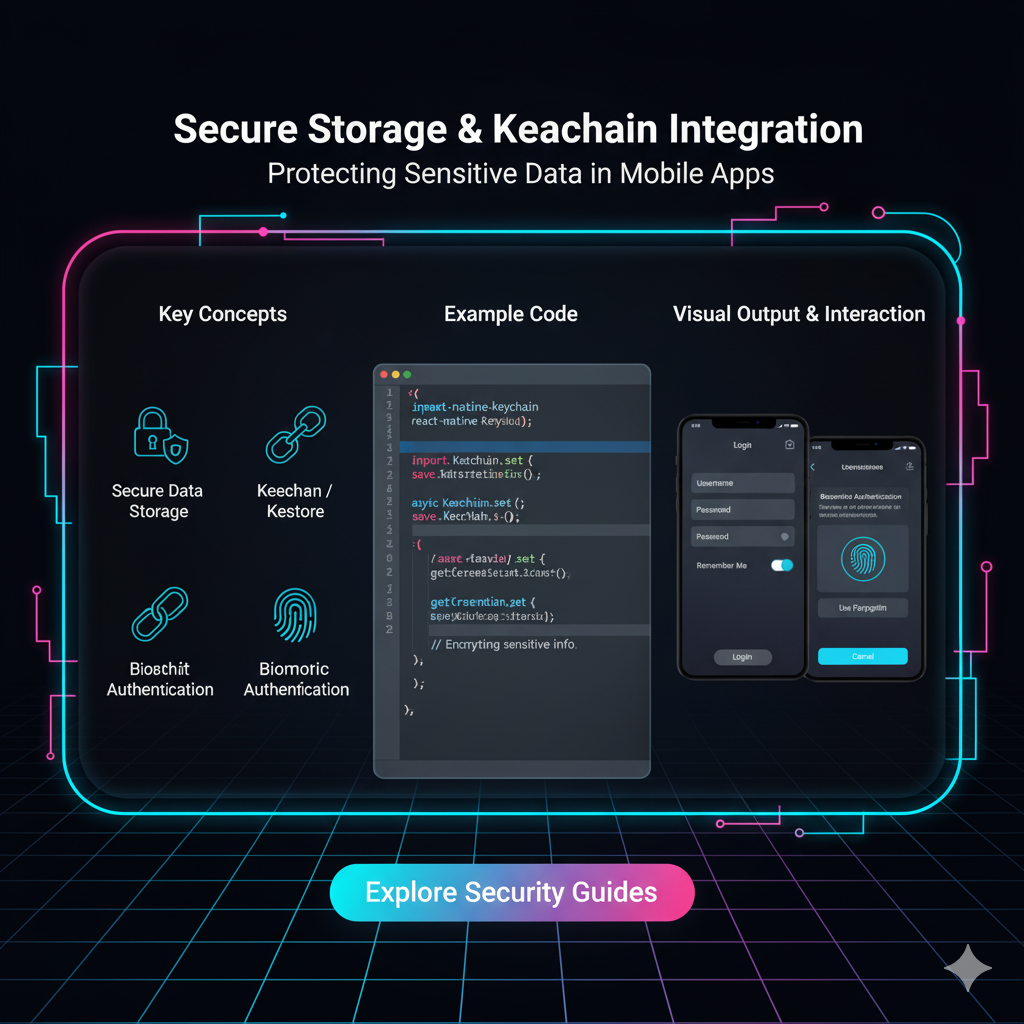
Meet the Guardians: Keychain (iOS) and Keystore (Android)
Both Apple and Google provide built-in, hardware-backed vaults for this exact purpose. They are the gold standard for on-device secret storage.
The iOS Bouncer: Keychain Services
Think of the iOS Keychain as a heavily fortified, encrypted database on the device. It's not just for Safari passwords; your apps can (and should!) use it too.
How it Works: Items you store in the Keychain are encrypted by the system. On devices with a Secure Enclave (modern iPhones/iPads), the encryption keys are stored in this separate, hardware-level chip, making them nearly impossible to extract.
The Cool Part: You can set accessibility attributes. For example, you can store an item that is:
kSecAttrAccessibleWhenUnlockedThisDeviceOnly: Only accessible when the device is unlocked, and it never leaves this specific device (not even in iCloud backups). This is the most secure option for most use cases.
The Android Vault: Keystore System
Android's answer is the Keystore system. It provides a container for storing cryptographic keys and, in later versions, general secret data.
How it Works: The Keystore lets you generate and store cryptographic keys in a way that makes it difficult to extract them from the device. The private keys never enter your app's process; you just ask the Keystore to perform operations with them (like signing or decryption).
For General Data: For stuff like API keys or tokens, you'd typically:
Generate a symmetric key inside the Keystore.
Use that key to encrypt your secret data.
Store the encrypted data in
SharedPreferencesor a database.When you need the data, ask the Keystore to decrypt it.
This means even if someone gets the encrypted blob, they can't do anything without the key, which is securely tucked away in the Keystore.
Real-World Use Cases: This Isn't Just Theory
Let's make this tangible. When would you actually use this?
Biometric Authentication: You store an encrypted token in the Keychain/Keystore with a rule that says "this can only be accessed after a successful Face ID or fingerprint scan." The app can't retrieve the token to authenticate the user without the user proving their physical presence.
Secure Offline Login: Instead of asking for a password every time, your app can store a secure, time-limited session token. When the app launches, it checks the Keychain/Keystore for a valid token to log the user in automatically—without exposing the token to other apps or system backups.
Protecting Third-Party API Keys: You have a paid service with a secret key. Hardcoding it in your app is a massive risk (people can decompile your app and steal it). A more secure method is to have your own backend issue a time-limited access token to the app, which is then stored securely on the device.
Best Practices: Don't Just Use It, Use It Right
Using the Keychain/Keystore is step one. Using it correctly is what separates the pros from the amateurs.
Know Your Accessibility/KeyGuard Flags: Don't just use the default. Choose the strictest accessibility option that still allows your app to function. For most user data,
ThisDeviceOnlyandWhenUnlockedare your best friends.Use Abstraction Libraries (Seriously): Dealing with the raw C APIs for Keychain or the complex Keystore API can be a pain. Use well-maintained, open-source libraries that provide a simple, cross-platform interface.
React Native:
react-native-keychainor@react-native-async-storage/async-storagewithreact-native-encrypted-storage.Flutter:
flutter_secure_storage.Native: For Android, use the
Securitylibrary from Jetpack.
Have a Clear Data Lifecycle: What happens when a user logs out? You must wipe the secure storage. What happens on a fresh install? Plan for when the data isn't there. Clean up after yourself.
Combine with Other Security Layers: Secure storage is one layer of the onion. Also use:
Certificate Pinning: To prevent man-in-the-middle attacks.
Code Obfuscation: To make reverse-engineering harder.
A Secure Backend: Because the strongest lock on your front door is useless if your back window is wide open.
Building secure applications requires a deep understanding of these concepts and how they fit together in a full-stack environment. To learn professional software development courses such as Python Programming, Full Stack Development, and MERN Stack, visit and enroll today at codercrafter.in. Our courses are designed to teach you not just how to code, but how to build robust, secure, and scalable applications from the ground up.
FAQs: Your Burning Questions, Answered
Q1: Is it 100% unhackable?
Nothing is 100% secure. However, Keychain and Keystore raise the bar extremely high. A hacker would need physical access to a unlocked device and sophisticated tools to even have a chance. It's about making the cost of a breach higher than the value of the data.
Q2: Can I use it with cross-platform frameworks like React Native or Flutter?
Absolutely! That's where the abstraction libraries we mentioned earlier come in. react-native-keychain and flutter_secure_storage act as bridges, allowing you to write one set of code that correctly uses the native secure storage on both platforms.
Q3: What happens to the data when the user uninstalls the app?
On iOS, if the item is stored with ThisDeviceOnly, it's gone forever when the app is uninstalled. On Android, it depends, but generally, Keystore keys are also tied to the app's lifecycle and are destroyed on uninstall. This is a good thing for security!
Q4: Should I store everything in secure storage?
No. It's overkill and can impact performance. Use it only for the most sensitive credentials and keys. For regular user preferences, use AsyncStorage or SharedPreferences.
Conclusion: Security is a Feature, Not an Afterthought
In the end, integrating secure storage isn't a "nice-to-have" advanced topic. It's a fundamental part of being a professional developer in 2024. Taking the extra hour to use the Keychain or Keystore instead of a quick-and-dirty solution is what separates a toy app from a production-ready, trustworthy product.
Your users may never know you did it, but they'll definitely feel the safety and reliability. And you'll sleep better at night knowing you're not the one who left the digital keys under the mat.
So, go ahead, open that project you've been working on, and do a quick audit. Are you storing any secrets in plain text? If the answer is yes, you now have the knowledge to fix it. Go build something awesome—and secure.
Ready to master the skills needed to build secure, enterprise-level applications? Dive deep into backend logic, frontend frameworks, and crucial security practices with our project-based courses. Check out our professional software development courses such as Python Programming, Full Stack Development, and MERN Stack at codercrafter.in and enroll today!